Many people mix up the dark web vs. deep web, but they’re actually very different parts of the internet. This guide is for anyone curious about what lies beneath the surface web—from students researching online privacy to professionals wanting to understand cybersecurity basics.
The confusion makes sense since both are hidden from Google searches. However, the deep web includes everyday sites like your online banking and private social media accounts, while the dark web requires special software and hosts anonymous marketplaces.
We’ll break down what makes the deep web different from the regular internet you use daily, explain how the dark web actually works and why people access it, and clear up the biggest myths about both. You’ll walk away knowing exactly which is which and why it matters for your digital safety.
Understanding the Surface Web vs Hidden Internet Layers

How search engines index only 4% of total internet content
When you perform a Google search, you’re only scratching the surface of what’s actually available online. Search engines like Google, Bing, and Yahoo crawl and index roughly 4% of all internet content. That means 96% of web pages, databases, and digital resources remain completely invisible to traditional search methods.
This limitation exists because search engine crawlers can only access publicly available pages with direct links. They follow hyperlinks from one page to another, building an index of discoverable content. However, vast portions of the internet exist behind barriers that these automated crawlers simply cannot penetrate.
| Search Engine Coverage | Percentage |
|---|---|
| Indexed by major search engines | ~4% |
| Unindexed internet content | ~96% |
Why billions of web pages remain invisible to Google and Bing
Several technical and structural barriers prevent search engines from accessing the majority of web content. Password-protected sites represent one major category of hidden content. Your personal email inbox, online banking portal, and private social media profiles all contain billions of pages that require authentication to access.
Dynamic content generated by databases creates another massive blind spot. When you search for flights on travel websites, the results page gets created in real-time from database queries. These temporary, personalized pages don’t have permanent URLs for search engines to index.
Private networks and intranets house enormous amounts of corporate and institutional data. Company databases, academic research repositories, government records, and medical systems operate on closed networks that deliberately exclude external access.
Form-based content presents additional challenges. Many websites hide their most valuable information behind search forms or user inputs. Real estate listings, job boards, and product catalogs often require specific search parameters to generate results pages.
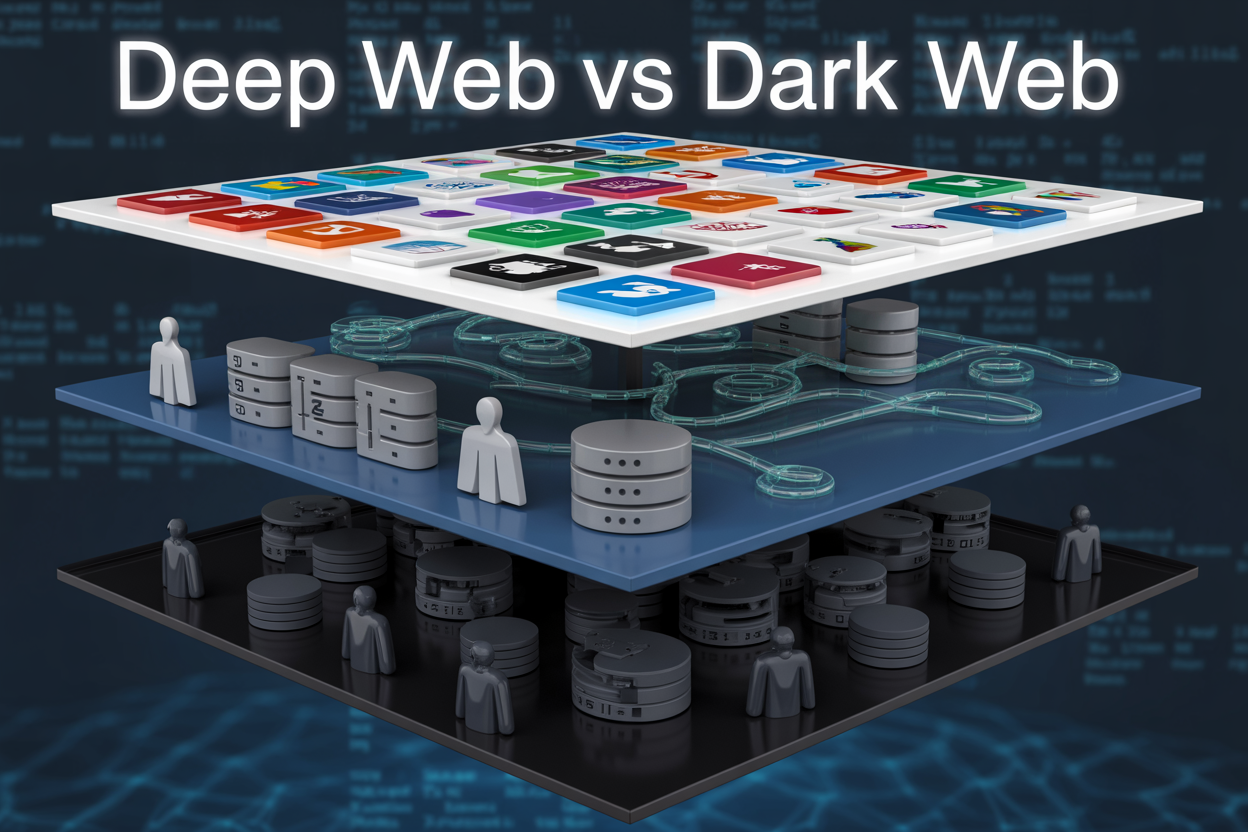
The iceberg analogy that explains internet accessibility levels
The internet’s structure closely resembles an iceberg floating in the ocean. The small tip visible above water represents the surface web – everything you can find through Google searches. This includes news websites, blogs, online stores, and public information that anyone can access without special tools or permissions.
Just below the waterline lies the deep web, representing the massive bulk of the iceberg hidden beneath the surface. This layer contains legitimate but private content like email servers, banking systems, private databases, and password-protected sites. While much larger than the surface web, the deep web consists primarily of mundane, everyday digital infrastructure.
At the very bottom of the iceberg sits the dark web – a small but highly specialized portion requiring specific software and knowledge to access. This deepest layer operates on encrypted networks designed for anonymity and privacy.
The proportions mirror real internet statistics: if the entire iceberg represents all internet content, only the tiny visible tip corresponds to search engine results, while the hidden underwater mass contains everything else we use daily but never see in search results.
Deep Web Fundamentals and Common Examples

Password-protected sites and private databases you access daily
Think about your typical day online. When you log into your email, check your bank balance, or browse your private social media profile, you’re actually diving into the deep web without even realizing it. These password-protected areas represent the largest portion of deep web content that regular users encounter.
Your Gmail inbox, Facebook timeline, and online banking portal all exist behind authentication barriers that search engines can’t crawl. Even subscription-based news sites like The New York Times or streaming platforms like Netflix house their content in the deep web. The moment you enter credentials to access personalized information, you’ve crossed from the surface web into deeper territory.
Cloud storage services like Google Drive, Dropbox, and iCloud also live in this space. Your personal documents, photos, and files remain invisible to search engines and other users unless you specifically share them. This everyday interaction with the deep web demonstrates just how normal and essential these hidden layers of the internet have become to modern digital life.
Corporate intranets and academic research repositories
Companies worldwide rely heavily on internal networks that exist entirely within the deep web. Employee portals, project management systems, and internal communication platforms create vast digital ecosystems that remain completely isolated from public view. These corporate intranets often contain sensitive business data, strategic plans, and proprietary information that organizations need to keep secure.
Academic institutions operate similarly sophisticated deep web infrastructures. Universities maintain extensive research databases, student information systems, and digital libraries that require proper authentication to access. Research papers, thesis collections, and scholarly articles often reside behind paywalls or institutional access controls.
Professional databases like LexisNexis for legal research, medical databases for healthcare professionals, and industry-specific repositories serve specialized communities. These platforms contain valuable information that justifies their protected status, creating legitimate reasons for deep web existence while serving important societal functions.
Medical records and financial account pages
Healthcare systems store patient records in secure, HIPAA-compliant databases that exist deep within protected networks. Your medical history, test results, and treatment plans live in electronic health record systems that only authorized medical professionals can access. These systems prioritize patient privacy while enabling healthcare providers to share critical information when needed.
Financial institutions operate some of the most secure deep web environments. Your checking account details, investment portfolios, credit reports, and loan applications all reside in heavily encrypted databases. Banks invest millions in cybersecurity to protect these systems from unauthorized access while providing customers convenient online access to their financial information.
Insurance companies, government benefit systems, and tax preparation services create additional layers of protected financial data. The IRS maintains taxpayer information in deep web systems, while Social Security Administration databases track benefit distributions and eligibility records.
Legal and legitimate reasons for deep web existence
The deep web exists primarily to protect privacy and secure sensitive information rather than hide illegal activities. Organizations have compelling legal requirements to restrict access to certain data types. GDPR in Europe, HIPAA in healthcare, and SOX compliance in finance all mandate specific data protection measures that naturally create deep web environments.
Intellectual property protection drives many businesses to maintain private databases and development environments. Software companies test new products in isolated deep web spaces, while pharmaceutical companies protect research data during drug development processes.
Government agencies operate extensive deep web systems for national security, public safety, and administrative functions. Census data, law enforcement databases, and diplomatic communications require protection from public access while remaining accessible to authorized personnel. These legitimate uses demonstrate that the deep web serves essential functions in our digital society, protecting everything from personal privacy to national interests.
Dark Web Architecture and Access Requirements

Tor Browser and Onion Routing Technology Explained
The dark web operates on a completely different technical foundation than regular websites. At its core lies the Tor network (The Onion Router), which creates multiple layers of encryption around your data—like peeling an onion. When you send information through Tor, it gets wrapped in several encrypted layers and bounced through at least three random servers called nodes or relays before reaching its destination.
Each relay only knows the previous and next step in the chain, never the complete path from you to the website. The entry node sees your real IP address but doesn’t know your final destination. The middle relay knows neither your identity nor your destination. The exit node sees the website you’re visiting but has no clue who you are. This creates a powerful anonymity shield that makes tracking nearly impossible.
Dark web websites use special .onion addresses that look like random strings of letters and numbers—something like “3g2upl4pq6kufc4m.onion” instead of regular domains. These addresses only work within the Tor network and can’t be accessed through regular browsers.
Why Specialized Software Is Necessary for Dark Web Navigation
Regular browsers like Chrome, Firefox, or Safari simply can’t access dark web content because they don’t understand the onion routing protocol. You need the Tor browser, which is essentially a modified version of Firefox designed specifically to work with the Tor network.
The Tor browser comes pre-configured with all the necessary settings to protect your privacy. It automatically routes all traffic through the Tor network, disables plugins that could leak your real IP address, and includes other security features like blocking scripts and preventing browser fingerprinting.
Other specialized software exists for accessing different dark web networks. I2P (Invisible Internet Project) uses garlic routing, similar to onion routing but with some technical differences. Freenet creates a decentralized network where content gets distributed across multiple nodes. Each requires its own specific software to access.
The Intentional Anonymity Features That Define Dark Web Spaces
Dark web platforms are built from the ground up with anonymity as the primary goal. Unlike regular websites that often collect user data, dark web services typically:
- Never log IP addresses or connection details
- Use cryptocurrency payments like Bitcoin or Monero to avoid financial tracking
- Require no personal information for account creation
- Employ end-to-end encryption for all communications
- Automatically delete data after specified time periods
Many dark web marketplaces and forums use escrow systems and reputation networks that work without revealing real identities. Users build trust through pseudonymous interactions over time rather than verified personal information.
The architecture itself prevents many common tracking methods. JavaScript often gets disabled by default, cookies work differently, and the browser regularly clears stored data. These aren’t just privacy features—they’re fundamental design principles that make the dark web function as an anonymous space.
Even law enforcement faces significant challenges when investigating dark web activities because the technology genuinely obscures user identities and locations when used correctly.
Key Differences Between Deep Web and Dark Web Content

Legal vs Potentially Illegal Content Distinctions
The deep web primarily houses perfectly legal content that simply requires authentication or direct access. Your private email inbox, online banking portal, medical records, and subscription-based academic databases all live here. These are legitimate services that businesses and individuals rely on daily. The content exists behind paywalls or login screens for privacy and security reasons, not because there’s anything questionable about it.
The dark web tells a different story. While it does contain some legitimate content like private communication tools and censorship-resistant platforms, it’s also notorious for hosting illegal marketplaces. Drug trafficking, weapons sales, stolen data markets, and other criminal enterprises find refuge in the dark web’s anonymity. This doesn’t mean everything on the dark web is illegal, but the proportion of questionable content is significantly higher than what you’d find in the deep web.
Privacy Protection vs Anonymity for Illicit Activities
Deep web privacy serves legitimate purposes. When you log into your bank account, the privacy protections keep your financial information secure from unauthorized access. Medical portals protect sensitive health data, and corporate intranets safeguard business information. The privacy here follows legal frameworks and regulatory compliance requirements.
Dark web anonymity operates differently. While journalists, activists, and whistleblowers in oppressive regimes genuinely need this level of anonymity for protection, the same tools enable criminal activities. The Tor network’s layered encryption makes it nearly impossible to trace users, which attracts both legitimate privacy seekers and those looking to hide illegal transactions.
Accessibility Barriers and Technical Requirements Compared
Accessing the deep web requires minimal technical knowledge. You need the right credentials – a username and password, a subscription, or institutional access. Most people interact with the deep web daily without realizing it. When you check your private social media messages or access your company’s internal documents, you’re using the deep web through standard browsers and familiar interfaces.
Dark web access demands more technical expertise. You’ll need specialized software like the Tor browser, understanding of .onion URLs, and knowledge of security practices to browse safely. The learning curve is steeper, and the user experience is often slower and more complex than surface web browsing. Many dark web sites require additional verification steps or invitation codes, creating multiple layers of access barriers.
Size and Scope Differences Between the Two Networks
The deep web dwarfs both the surface web and dark web in size. Estimates suggest it’s 400 to 500 times larger than the surface web, containing massive databases, private documents, and secure systems across countless organizations worldwide. Every company with an intranet, every university with student records, and every government agency with internal documents contributes to this vast repository.
The dark web represents a tiny fraction of the overall internet – roughly 0.01% of the total web. Despite its outsized reputation, it contains far fewer sites and users than either the surface or deep web. The dark web’s impact on popular culture and media attention far exceeds its actual size, creating a perception that it’s larger and more prevalent than reality suggests.
Common Misconceptions and Security Realities

Why the deep web isn’t inherently dangerous or criminal
The deep web gets a bad rap that it simply doesn’t deserve. Most people imagine shadowy criminal networks when they hear “deep web,” but the reality is far more mundane. Your online banking account, private email inbox, medical records, and subscription-based content all live on the deep web. These are just regular websites that require passwords or special access to view.
Think about it this way: every time you log into your Gmail account, you’re accessing the deep web. When you check your student grades online or view your health insurance portal, that’s deep web content too. The defining characteristic isn’t criminal activity – it’s simply that search engines can’t crawl and index this content because it sits behind authentication barriers or exists as dynamically generated pages.
Companies like Netflix, Amazon Prime, and academic databases make up huge portions of the deep web. Library systems, corporate intranets, and government employee portals all contribute to this hidden layer of the internet. None of these services are designed for illegal activities; they’re just not meant for public viewing without proper credentials.
The confusion often stems from conflating the deep web with the dark web. While the dark web represents a tiny fraction of the deep web, media coverage tends to paint the entire deep web with the same brush, creating unnecessary fear around perfectly legitimate online spaces.
Legitimate uses for dark web privacy and anonymity tools
The dark web serves several legitimate purposes that have nothing to do with illegal marketplaces. Journalists working in oppressive regimes rely on dark web tools to communicate with sources and publish sensitive information without facing persecution. The Tor browser, which provides access to the dark web, was originally developed by the U.S. Navy and continues to receive funding from government agencies because of its legitimate security applications.
Whistleblowers use dark web platforms to safely expose corporate wrongdoing and government corruption. Major news organizations like The New York Times, The Guardian, and ProPublica operate secure drop sites on the dark web specifically for receiving sensitive tips and documents. These platforms protect sources from retaliation while enabling important investigative journalism.
Privacy-conscious individuals living under authoritarian governments use the dark web to access blocked websites, communicate freely, and organize peaceful protests. During the Arab Spring, activists relied heavily on these tools to coordinate demonstrations and share information with the outside world.
Law enforcement agencies also use dark web tools for legitimate undercover operations and to investigate criminal activities. Security researchers access the dark web to study emerging threats and develop better protection measures for organizations and individuals.
Even in democratic countries, the dark web provides valuable privacy protection for people discussing sensitive topics like mental health, domestic abuse, or political dissent in regions where such discussions might put them at risk professionally or socially.
Real security risks vs media-driven fears about both networks
Media coverage of the deep and dark web often amplifies rare, extreme cases while ignoring the mundane reality that millions of people interact with these networks daily without incident. The actual security risks are more nuanced and manageable than sensationalized headlines suggest.
| Real Risks | Media-Driven Fears |
|---|---|
| Malware from untrusted downloads | Automatic infection from browsing |
| Scams targeting inexperienced users | Hackers tracking every click |
| Law enforcement monitoring illegal activities | Government surveillance of all users |
| Personal data exposure through poor security practices | Identity theft from mere access |
The biggest security risk for most users isn’t sophisticated cybercriminals – it’s basic digital hygiene failures. Reusing passwords, clicking suspicious links, and downloading files from untrusted sources pose far greater threats than simply accessing deep or dark web content.
For dark web users specifically, the main risks include encountering illegal content accidentally, falling victim to exit scams on marketplaces, and potential legal consequences if engaging in prohibited activities. However, simply accessing the dark web through Tor isn’t illegal in most countries, and the software includes built-in protections against many common threats.
The deep web presents even fewer risks since most interactions happen through legitimate, encrypted connections with established services. Your biggest security concern when accessing your bank account online should be ensuring you’re on the correct website and using strong authentication methods – not worrying about mysterious hackers lurking in the “deep web.”
Smart security practices – using updated software, enabling two-factor authentication, and being cautious about downloads and links – provide effective protection regardless of which layer of the internet you’re accessing.

The internet has three distinct layers, each serving different purposes and requiring different levels of access. The deep web contains everyday private information like your email inbox and bank accounts, while the dark web represents a small, encrypted corner that requires special software to reach. Most people confuse these two, but understanding their differences helps you navigate online security more effectively.
Both the deep web and dark web play important roles in internet privacy, though for very different reasons. The deep web protects your personal information from search engines, while the dark web offers anonymity for both legitimate privacy needs and illegal activities. Stay curious about how the internet works, but remember that your everyday browsing happens safely on the surface web where most legitimate online activities belong.

Saurabh Kumar is the founder of SaurabhOrbit.com, a hub for tech news, digital marketing insights, and expert blogging advice. With a deep passion for technology and digital strategies, Saurabh simplifies complex trends into actionable insights for readers looking to stay ahead in the digital world. My mission is to empower entrepreneurs, tech enthusiasts, and marketers with the latest tools and knowledge to thrive in the online space.